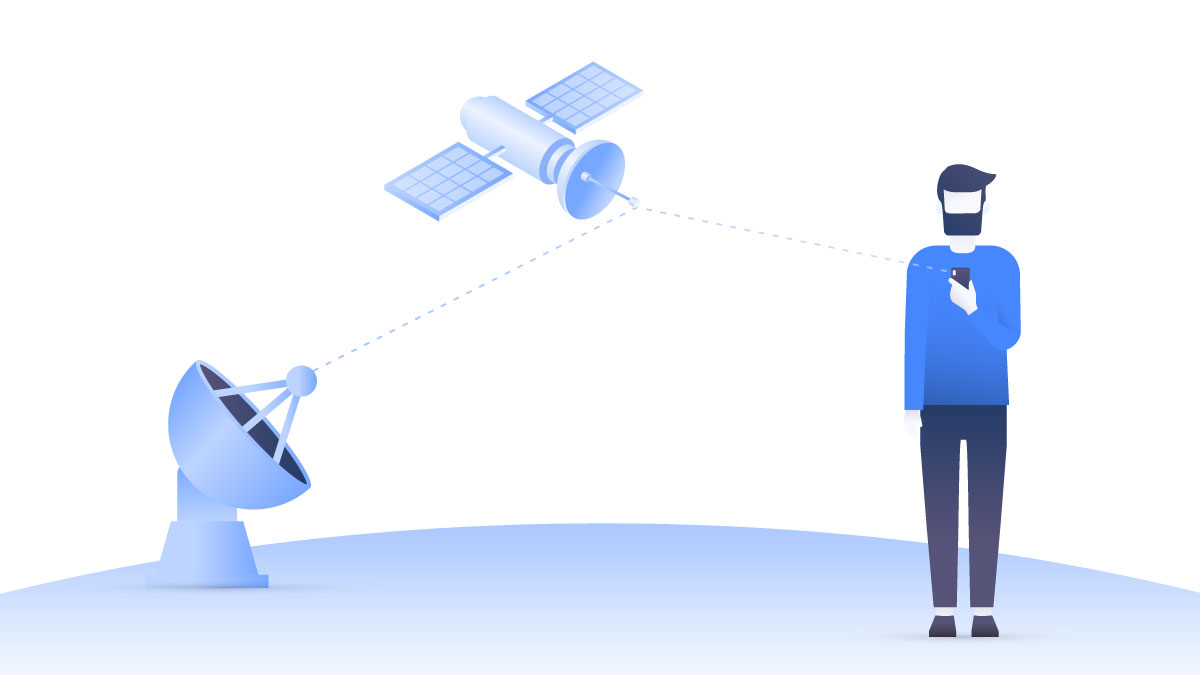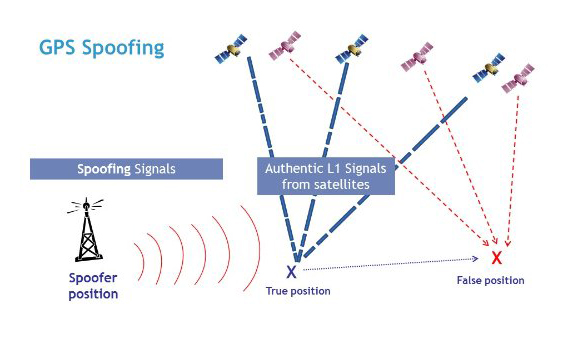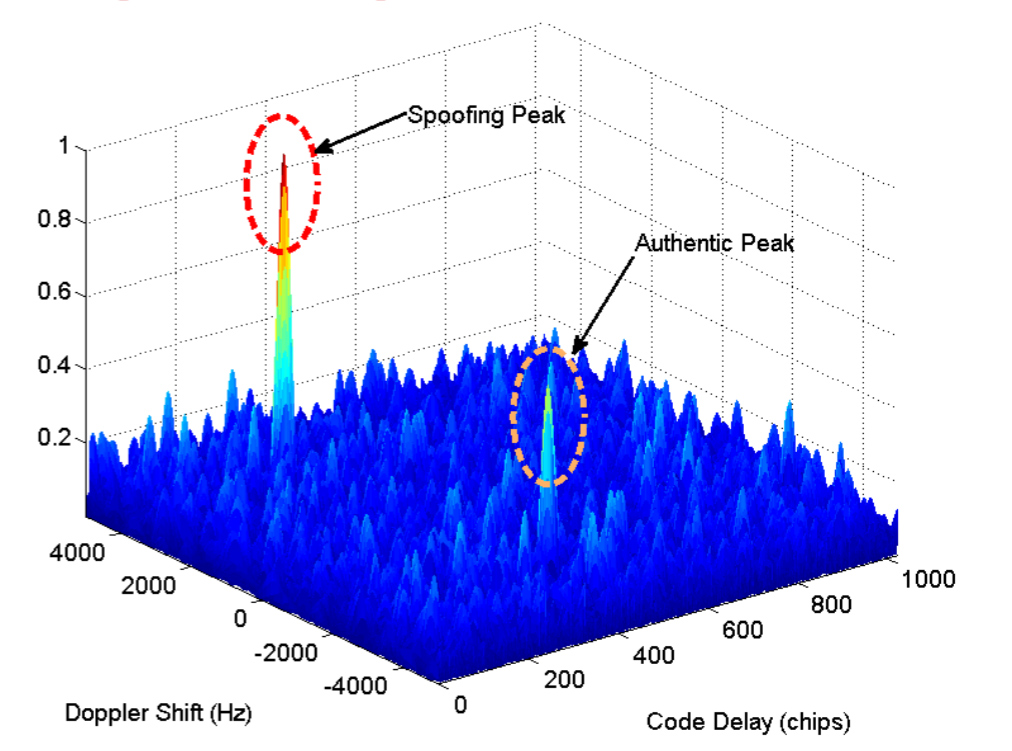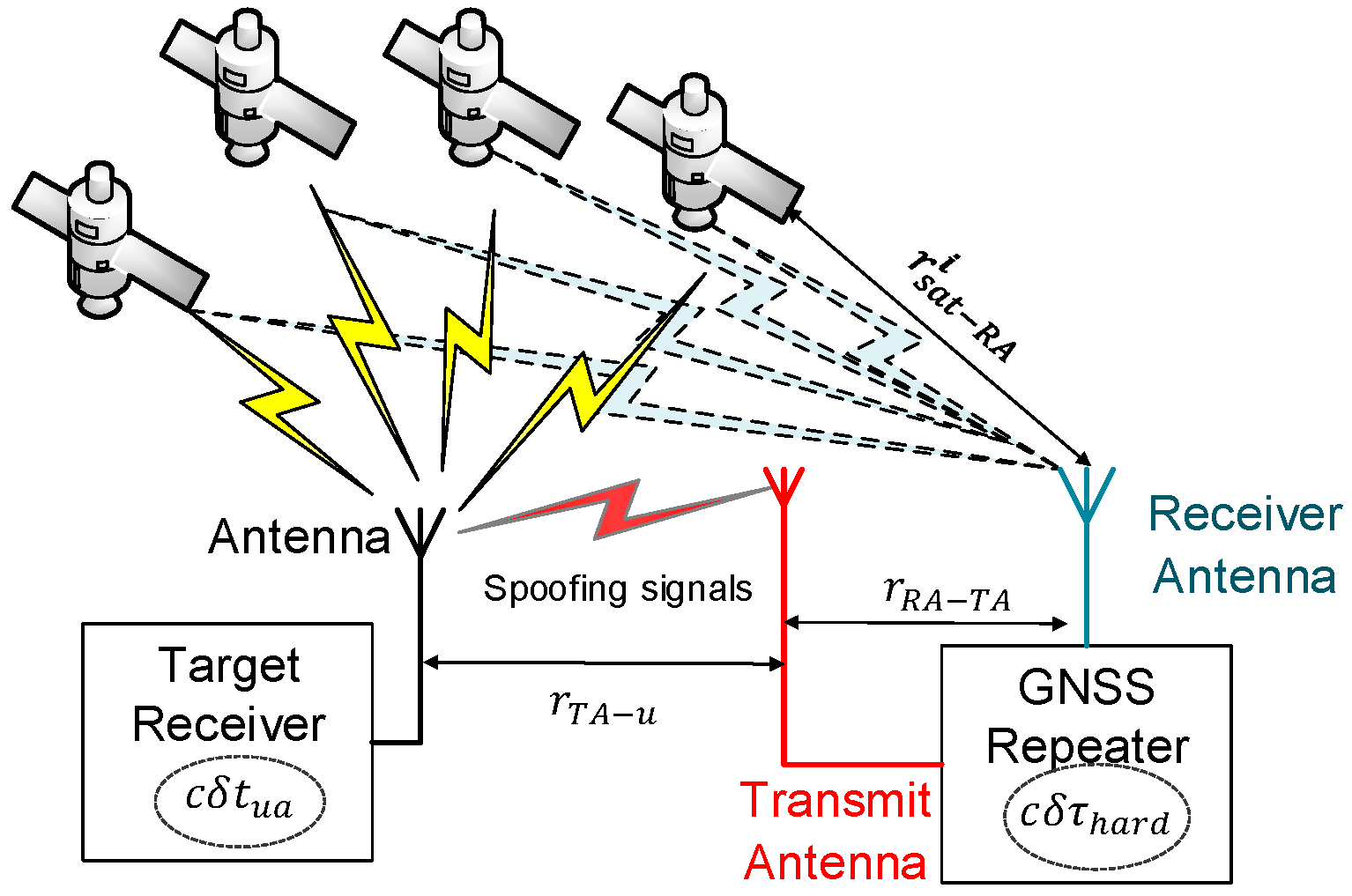
Sensors | Free Full-Text | Performance Analysis of GNSS/INS Loosely Coupled Integration Systems under Spoofing Attacks | HTML
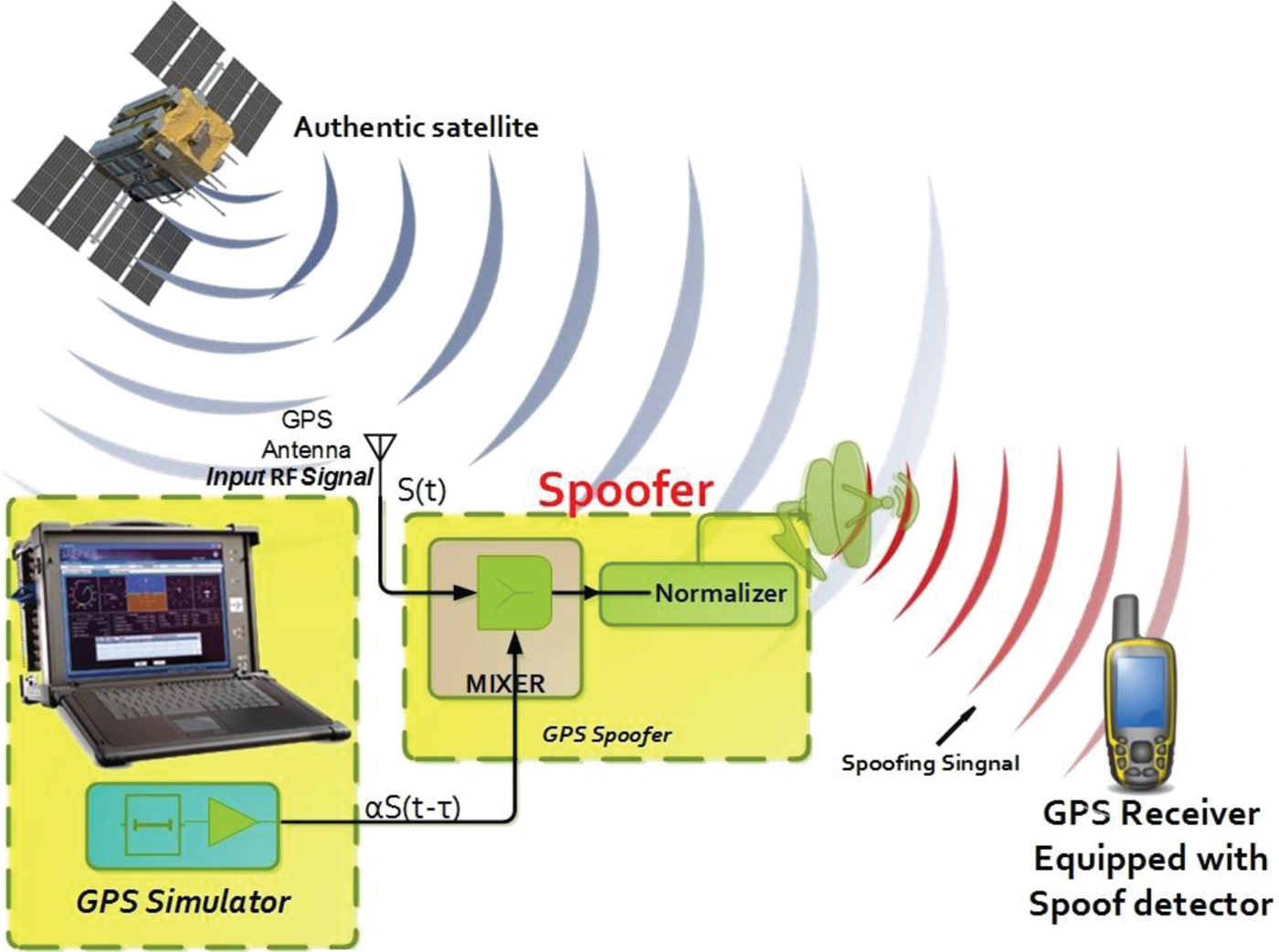
Detection of Spoofing Attack using Machine Learning based on Multi-Layer Neural Network in Single-Frequency GPS Receivers | The Journal of Navigation | Cambridge Core

Strategic Defense Against Deceptive Civilian GPS Spoofing of Unmanned Aerial Vehicles | Semantic Scholar

A Modified Imperialist Competitive Algorithm for Spoofing Attack Detection in Single-Frequency GPS Receivers | SpringerLink
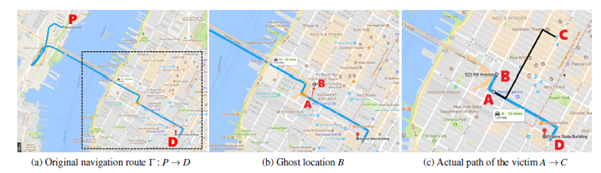
Oracle Knowledge InfoCenter - GPS Spoofing attack sends 38 drivers the wrong way - and into possible danger
![On GPS spoofing of aerial platforms: a review of threats, challenges, methodologies, and future research directions [PeerJ] On GPS spoofing of aerial platforms: a review of threats, challenges, methodologies, and future research directions [PeerJ]](https://dfzljdn9uc3pi.cloudfront.net/2021/cs-507/1/fig-4-full.png)
![PDF] Quickest detection of GPS spoofing attack | Semantic Scholar PDF] Quickest detection of GPS spoofing attack | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1d9de7c96db03c87dd50c58348461c15b0c43de7/1-Figure1-1.png)